Automated Clearing House (ACH) Tokenization
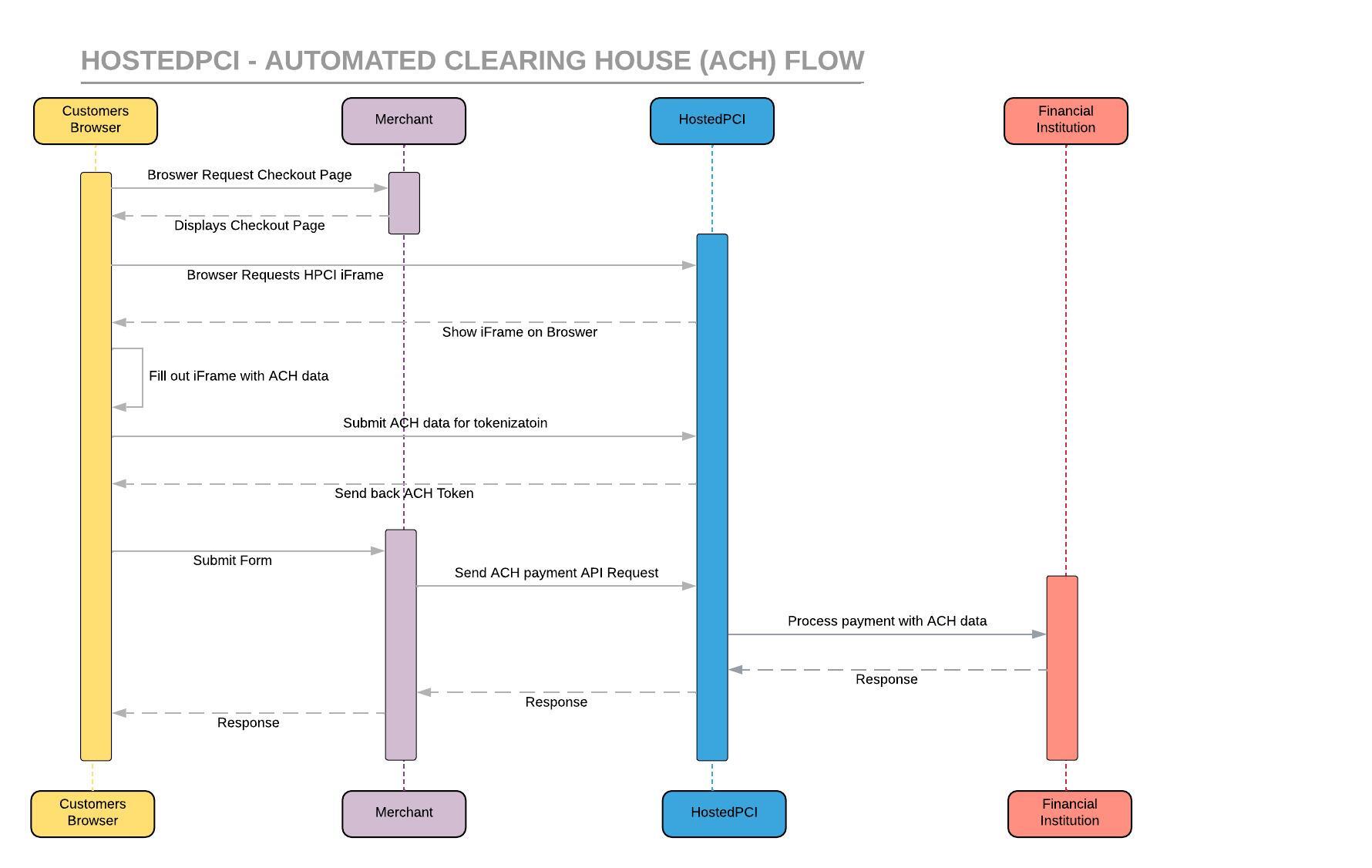
ACH tokenization is designed to safeguard sensitive financial data during electronic transactions. Our ACH tokenization solution replaces critical information, such as bank account numbers, with unique tokens. These tokens are randomly generated and intricately linked to the original data but are entirely meaningless to unauthorized parties. During the transaction, these tokens are transmitted instead of the actual financial details, ensuring that sensitive data remains hidden throughout the process.
The Merchant provides HostedPCI with the specific tokens that are required to be utilized for a payment and HostedPCI then detokenizes the token and forwards the real data to the Financial institution. The detokenization process happens within HostedPCI, efficiently and securely while maintaining the real data protected. The fundamental benefit of ACH tokenization is its ability to enhance security significantly. Even if the HPCI tokens are accessed by malicious actors during a potential leak within the merchant’s environment, they are utterly useless for reverse-engineering to access the original data, providing an additional layer of protection. The fundamental benefit of ACH tokenization is its ability to enhance security significantly. Even if tokens are intercepted by malicious actors, they are utterly useless for reverse-engineering to access the original data, providing an additional layer of protection.
Additionally, our ACH tokenization solution is highly flexible and scalable, making it easy to integrate into existing systems. This adaptability ensures that the system can seamlessly grow and evolve alongside the organization’s needs.
In summary, ACH tokenization is a critical process that bolsters the security of electronic transactions involving sensitive financial information. By substituting sensitive data with tokens and enabling secure detokenization, it not only protects against data breaches but also ensures compliance with data security regulations, all while offering flexibility for businesses to adapt to changing needs. This approach reinforces overall transaction security in an increasingly digital landscape.

